
Your Easy Access Book: Masuk WhatsApp Web & Web Login Steps Staying connected is important. WhatsApp Web makes this easy. It mirrors your phone’s WhatsApp…

How Fintech Startups Are Reconceptualizing Access to Business Capital Securing funding has long been one of the steepest obstacles facing businesses—especially startups and small enterprises…

Halls of Amenti, Interdimensional Travel, Aliens! – Star In the large frontier where cosmic energy interlaces with human consciousness, one encounters phenomena like the mysterytic…

Real-Time Data contra Historical Data: Directing through Time-Turner of Analysis Methods Ah, data! The modern alchemist’s gold, turning ignorance into insight and spreadsheets into strategy.…

How to Avoid Data Swamp Problems in Your Data Lake Whether you’re a data analyst, IT manager, or data scientist, chances are you’ve heard (or even…

Databricks & Start Motion Media: Data Business Development Unleashed Data is the new oil, and in today’s dangerously fast time, exploiting its power means diving…

Introduction to the Evolution of Access Control Systems Other than new threats as a driving force for innovation in access control, technology advancements also play…

TL;DR In this covering report, we look at a complete analysis of all 10 seasons of Shark Tank – an American business reality television series,…

I’m ready to develop your report into a detailed, stirring piece incorporating the desired writing styles and awareness elements. Let’s start: “` Disclosure: Some links,…

The Bespoke of Autonomous Driving: A Glitchy Road to Days to Come The Autonomous Adventure: When Your Car Thinks It’s the Boss Welcome to the…

the Mysteries of Venn Diagrams: Virtuoso the Art in PowerPoint with Flair In the incredibly focused and hard-working world of business presentations, where every pie…
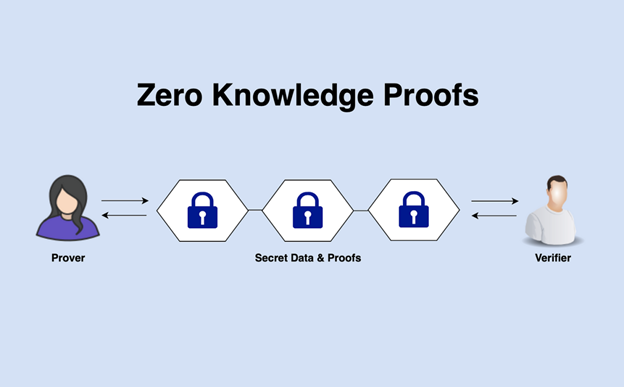
How Zero-Knowledge Proofs Are Transforming Authentication Systems Disclosure: Some links, mentions, or brand features in this article may reflect a paid collaboration, affiliate partnership, or…

5 Practical Steps To Avoid Identity Theft Millions fall victim to identity theft annually, through stolen credit card numbers or fake accounts. For identity thieves,…

Network infrastructure is the central support or structure for the transmission of information in the interconnected world of today. The basic parts of any network…

Cloud computing has revolutionized the way businesses manage and store their data. It offers a memorable many advantages, including scalability, cost-efficiency, and flexibility. But if…













